Scam-baiting YouTube channel Scam Sandwich exposes ‘Expert Tech Solutions’, a Pakistan-based online scam operation
by Dr. Piyush Mathur
This scam company called Expert Tech Solutions impersonates Canadian telecommunications companies—like Telus, Rogers, Bell Canada and Koodo—in order to gain access to their victims’ accounts and then use their victims’ money to purchase smartphones, which they will then sell for profit.
Thus starts a clinical, darkly funny exposé of a Pakistani online scam call centre by the investigative-hacker YouTube channel Scam Sandwich! The video (uploaded on March 18, 2025) soon shows Noman, one of the alleged scammers (caught on video via the hacked cameras) bluntly repeat to an alert target—who had asked him why they scam people—that ‘scamming people’ was his job!
Before getting to the rest of the gripping and eye-opening details of this alleged (and apparent) scam operation, it should be noted that this writer has no clue to the actual identity of the person behind Scam Sandwich, whose narration is always in a natural-sounding male voice in American accent—and which drops all sorts of indications that the person is an American male. But it might as well be a group of people, perhaps led by one person (who might even be a female or some other gender). At any rate, ‘Scam Sandwich’ would be referred to as ‘the channel’ or a ‘he’ in the rest of this report.
Per his account, Scam Sandwich was able to establish the physical location of the scamming outfit by mapping out all ‘the nearby Wi-Fi networks and their signal strengths’ through its workstations. Via online video surveillance inside the outfit’s office building’s elevator lobby, the channel was also able to pinpoint the floor within the posh, 19-storey Ali Tower in Lahore’s Gulberg area that these scammers used as their workspace. (Ali Tower also happens to have a McDonald’s outlet, proudly mentioned on the Ali Group’s website advertising the tower.) Scam Sandwich identifies the floor as Floor E, situated between Floor P2 and Floor 1.
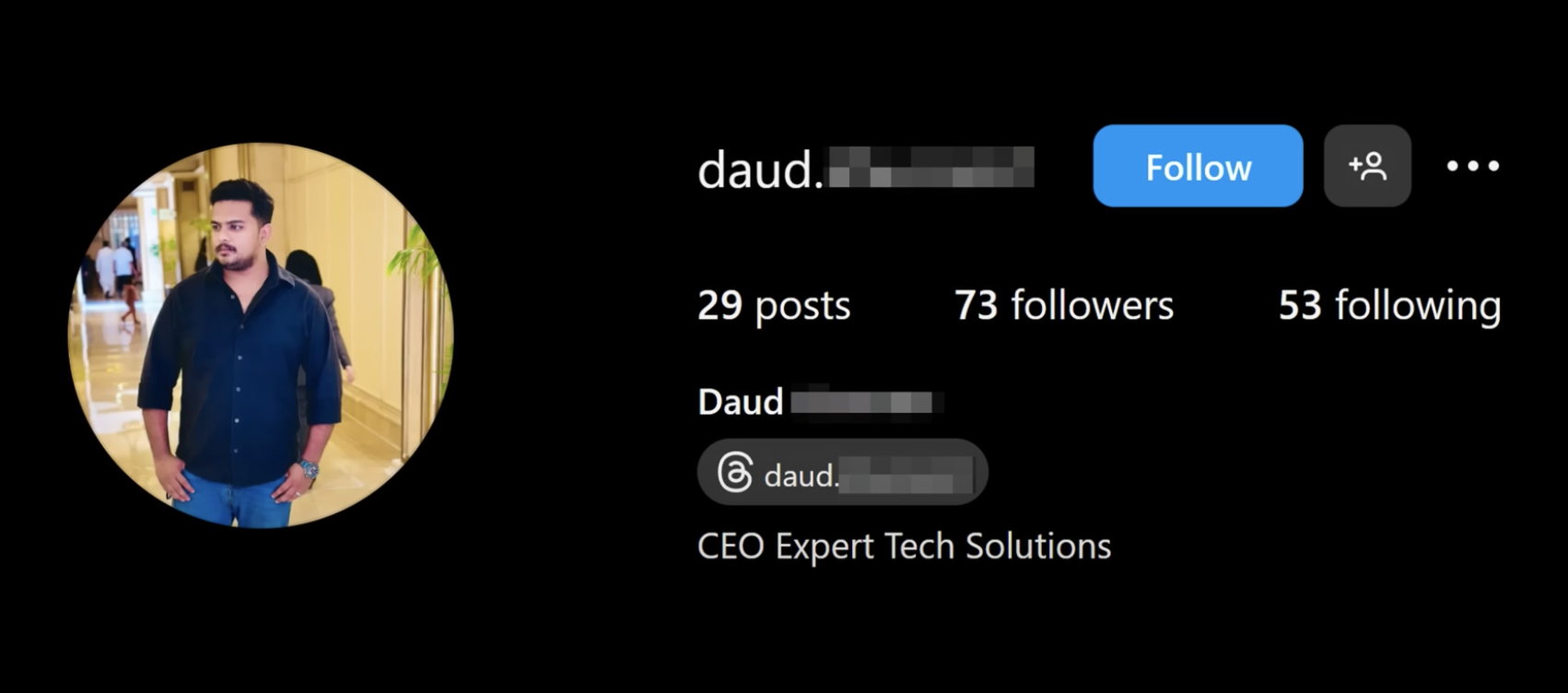
Screenshots related to Daud, the self-proclaimed Chief Executive Officer (CEO) of Expert Tech Solutions, the Lahore-based online fraud outfit with an office in the posh Ali Tower. These screenshots have been taken from Scam Sandwich’s investigative hacker video uploaded to YouTube.
Daud, staring into the hacked camera
Daud on Instagram
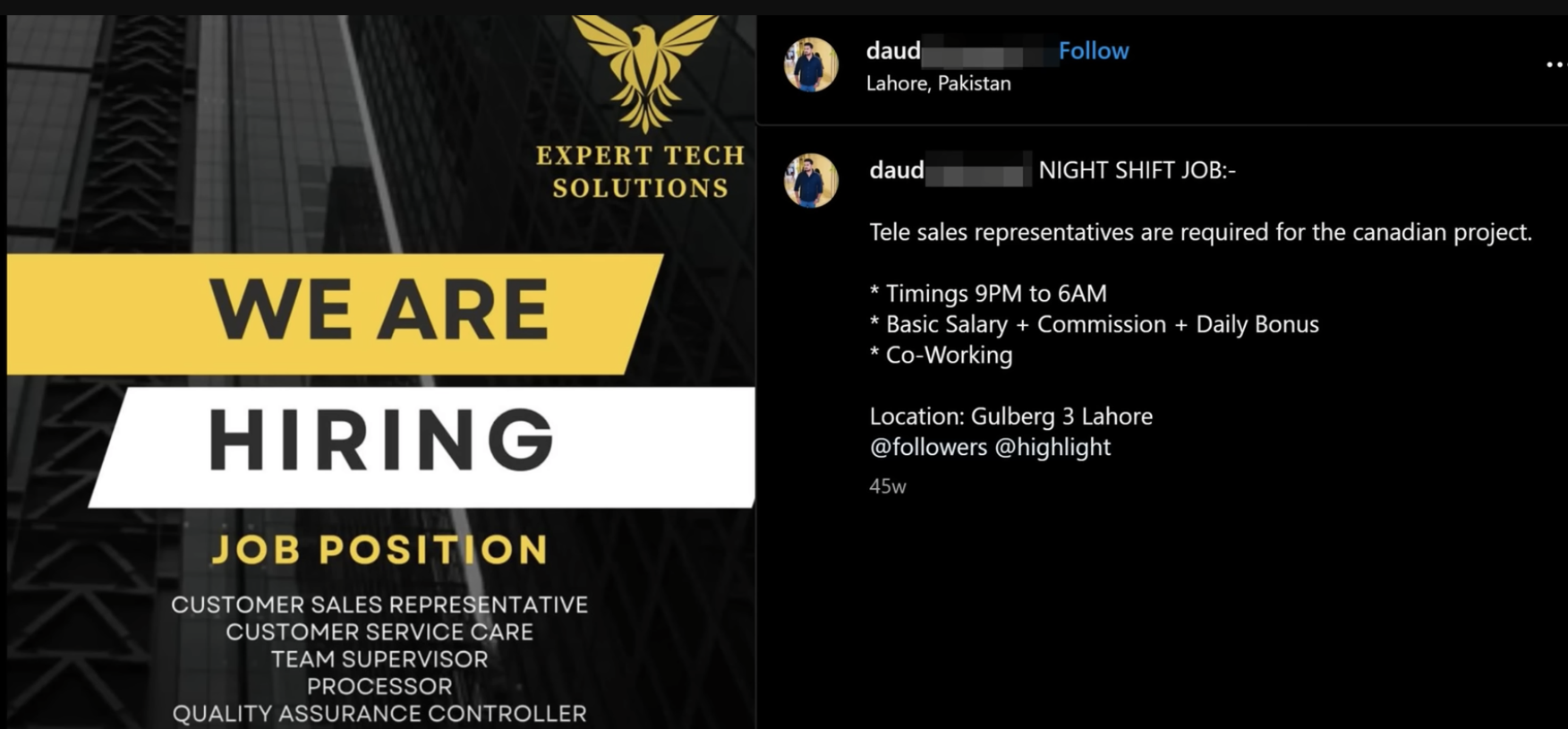
Recruitment advertisement posted by Daud on his Instagram account.
The text ‘Daud’ was an annotation made by Scam Sandwich next to this screenshot of Daud’s social-media photograph included in the channel’s uploaded YouTube video.
Jawad, who called himself ‘Sunny’ in his scam
call to a Canada resident.
Expert Tech Solutions’ modus operandi
Next, offering a complete sample of the scammers’ modus operandi, Scam Sandwich shows audio-visual footage of the scammers’ interaction with a Canadian target-turned-victim.
The interaction starts out with one scammer, Jawad, introducing himself as ‘Sunny’ via a phone call to his target: a man who resides in Canada and owns a smartphone. ‘Sunny’ tells the target that he was calling on behalf of the telecommunications companies Telus and Koodo regarding an ongoing promotional campaign for the latest iPhone and Samsung smartphone models (with the fictional scheme including cheap SIM plans as well as a 40% discount on the new model).
Omar, a key scammer,
as identified by Scam Sandwich
He goes on to ask the target what phone model he had. The unsuspecting target tells ‘Sunny’ that he had a Samsung S-20. By this point, the target is already a victim—say, of information theft via false impersonation on the part of the scammer. His financial victimisation, however, still awaits him—and it would be preceded by additional information theft.
‘Sunny’ tells the victim that he could send him Samsung S-24 as part of the discounted upgrade, wondering what he thinks of the offer. The victim tells him that the offer ‘does not sound too bad’ to him. ‘Sunny’ then asks the victim for his email address tied to Koodo under the pretext of needing to send him a confirmation email.
The victim shares his email address with him (though the channel conceals this part of the interaction from the viewers). ‘The scammer,’ Scam Sandwich tells us, ‘will now head over to the Koodo log-in page on his PC and attempt to reset the victim's password using the email address that he just received. This will send an email back to the victim with a link to reset their password.’
Once the victim receives that email, he tells the scammer that it contains a button asking him to reset his password—and whether he should press that button. The scammer reassures him that he needs to click that reset link and change his password to what he falsely calls a ‘promo password’ that he would supply.
When the victim clicks the reset button, the scammer supplies him with his own password—and the victim changes his original password to this faux ‘promo password’. Using this faux ‘promo password’, the scammers are now also able to get inside the victim’s Koodo account—and see the last four digits of the victim’s credit card registered with Koodo. (Meanwhile, the victim asks again about the upgraded model that he would be getting, and ‘Sunny’ repeats that it is S-24 Ultra-Samsung.)
At this point, as the channel explains (and as the viewer can also see on the screen), the scammer turns over the call to his team member, whose task is to get the victim’s full credit card number—without which Expert Tech Solutions would not be able to buy a new phone for itself via Koodo. The channel further explains that this second scammer (whom the viewer could see and hear declaring himself to the victim as ‘Brian Marshall’, his ‘account’s manager’) plays the role of a ‘closer’: as in the person who closes a transaction/deal.
Three key alleged scammers of the Lahore-based Experts Tech Solutions: Daud (black and grey jacket, holding a smartphone), Omar (white sweatshirt), and Umer (striped shirt). This is a partial screenshot from am investigative hacker video posted by Scam Sandwich, a YouTube channel.
Left to right: Daud, Umer, and Omar—three key scammers belonging to the Lahore-based outfit Expert Tech Solutions—in a social-media photograph.
This is a screenshot from an investigative video posted by Scam Sandwich, a YouTube channel.
The closer tells the victim that there is a delivery fee of $14.99, for which he needs to make ‘an upfront payment’ using his credit card (registered with Koodo, it is implied). The victim goes along with the new demands, and shares his full credit card number with the closer.
This is Bilal, one of the alleged key scammers captured in the hacked video footage by Scam Sandwich, a YouTube channel, which claimed that he has no active social-media account (in his own name); the channel also claimed that two of his associates, Daud and Faisal, accused him of being the mastermind.
Using that number, however, the closer can be seen placing an order for an iPhone 16 Pro Max device—and not the S-24 Ultra that had been promised the victim. The channel explains that these scammers ‘will always order the device opposite of what the victim wants’ so that they could regret their error to the victim and provide him (or her) ‘with a shipping label to return the incorrectly ordered phone’—except that the address on the label would be a residence in Brampton, Ontario, where their ‘money mule’ would ‘pick up the package’ and later sell it profitably ‘on the black market’.
Next in the video, reflecting the channel’s explanation, the closer transfers the call to the operation’s supervisor, Bilal, who introduces himself as ‘John from the Order Processing Team of Koodo’. This ‘John’ asks the victim whether he had received any email regarding the order. When the victim confirms having received an email from the company (showing an incorrect order, it is implied), ‘John’ tells him that this error of incorrect orders is common, and that the order would be corrected and the victim would receive its tracking number within the next 24 hours via a new email—and that he should ignore the email showing the incorrect order.
After filling out the victim’s details, Bilal takes the order form’s copy to the manager’s office, where the manager, Faisal, can be seen getting a head massage from his employees; in a prior snippet, one could see him getting a foot massage. (In a subsequent footage, the video also shows the exact cabinet in which these order forms’ copies are stored.)
Faisal, an alleged key scammer with Expert Tech Solutions, the Lahore-based fraudulent outfit, likes to get massages from his employees in his office. These are screenshots from am investigative hacker video posted by Scam Sandwich, a YouTube channel.
How did Scam Sandwich figure out the mule address?
Scam Sandwich had to call up one of the scammers, Shaheryar (whose fake name is John Marshall), and pretend that he was a customer who had received an incorrect phone and was still awaiting the return-address label. Shaheryar—who is later described in the video to be doing Human Resources (HR) duties as well as floor management—first asks him whether he had opened the parcel. Upon being assured that the parcel had not been opened, per the standing instructions, Shaheryar tells Scam Sandwich that he would send him a FedEx return address label via WhatsApp, and that he must take it to a FedEx centre along with the parcel.
Umer, a alleged key scammer who works for Expert Tech Solutions, a Lahore based online scam outfit. This is a screenshot of Umer photograph from an investigative hacker video posted by Scam Sandwich, a YouTube channel.
Daud, the self-proclaimed Chief Executive Officer (CEO) of Expert Tech Solutions, a Lahore-based scam call centre. This is a screenshot from am investigative hacker video posted by Scam Sandwich, a YouTube channel.
However, Scam Sandwich tells Shaheryar to simply text the return label on the number from which he was on the call with him; Shaheryar agrees to his suggestion and leaves it to Faisal to do this part of the job. Subsequently, we can see Faisal sending out that label and also calling Scam Sandwich to ensure that he had received the return-address label on his phone.
In the video, the viewer is shown that the return address is located in Brampton, Ontario; however, Scam Sandwich hides the rest of the address stressing that ‘it's not clear if this home is being occupied by a money mule or if the money mule simply waits at the address for the package to arrive using the FedEx tracking info.’
Why didn’t the scammers order the phone directly to their mule address?
What the channel does not explain is precisely why the scammers would need to order the device to the victim’s address—before getting him to return the received device to the mule address—instead of sending it directly to the mule address. One could speculate that they do so to avoid an automated prompt from Koodo notifying the victim of a change in their mailing address or because Koodo’s fraud detection system requires the shipping address to match the address on the credit card used, flagging the transaction until the registered customer approves it via an email link in case of a mismatch.
Or, these scammers want to delay suspicion from a victim—who could notice on his Koodo profile or via an order confirmation email that his or her order was destined for an unknown address, and call up the company or the bank to cancel the transaction well before the order is shipped. Or, these scammers use this indirect method because they appreciate the fact that a victim who would have actively participated in the process would be less likely to dispute the transaction; and if such a transaction is disputed or reported to law enforcement, then it won’t generate a clear trail back to them.
But perhaps the most compelling reason why this indirect method would be used by these scammers is that if they use a specific mule address for direct shipments, then Koodo may flag it after multiple fraud cases. Instead, by having the victims do the ‘return’ from their own addresses, the scammers get around Koodo's internal tracking and blacklist mechanisms.
‘Mobility’ & ‘air duct-cleaning’ faux enterprises
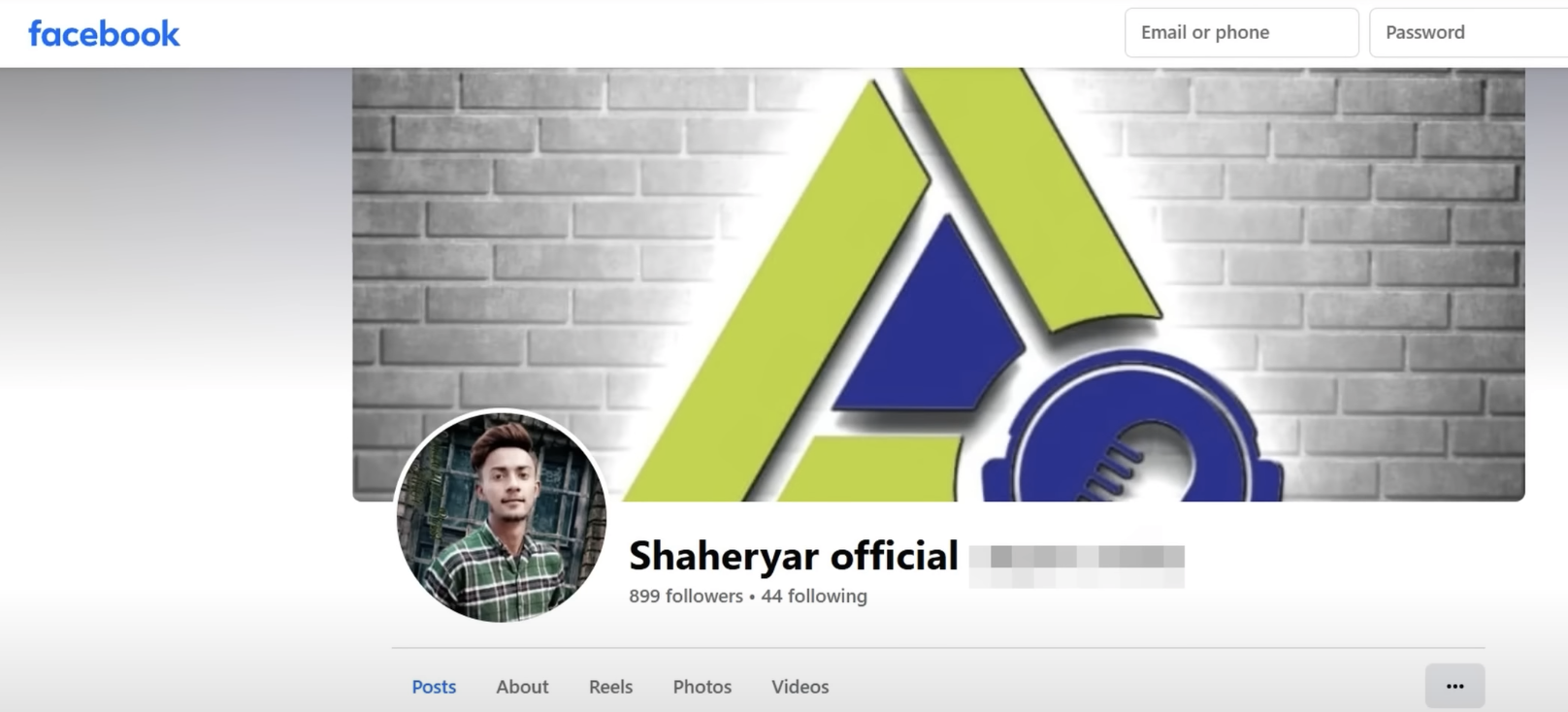
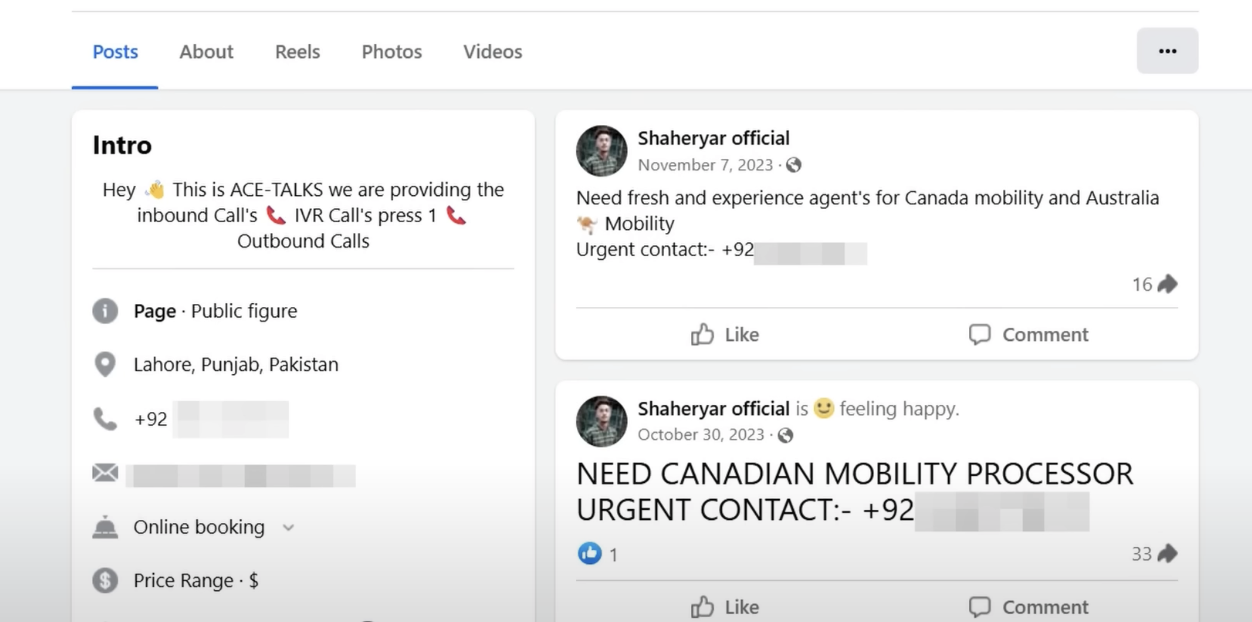
Later in the video, Scam Sandwich highlights the curious fact that these scammers refer to their smartphone stealing enterprise as ‘mobility’ business—something he discovered when he looked at some of their recruitment advertisements on social media and during his telephonic confrontations with some of them. For instance, Shaheryar, who tends to work as a ‘closer’, had also posted recruitment advertisements on his Facebook profile for ‘agent’s [sic] for Canada mobility and Australia Mobility’ and for ‘Canadian Mobility Processor’.
The Facebook profile page of Shaheryar, an alleged key scammer at the Lahore-based Experts Tech Solutions. This is a screenshot from am investigative hacker video posted by Scam Sandwich, a YouTube channel.
One alleged scammer, Shaheryar, posted the above advertisements on his Facebook profile for positions in Expert Tech Solutions, the Lahore-based fraudulent outfit. This is a screenshot from am investigative hacker video posted by Scam Sandwich, a YouTube channel.
A related curious fact revealed in the exposé is that these scammers share their roof with two rows of callers that are involved in an air duct cleaning campaign. Scam Sandwich, however, does not focus on these individuals—but he discovers some evidence that this air duct cleaning campaign targeting American households involves fraudulent marketing, which is generally investigated by his friend Pleasant Green (whose YouTube video can be watched here.)
First confrontation
Based upon months of research using the hacked machines—and full-on video surveillance of both the interior and exterior of the scammers’ office areas through the hacked cameras—Scam Sandwich decided that it was time to confront the scammers via a phone call even as he was surveilling them audio-visually.
His first call was made to Umer, a key scammer who was sitting with his colleagues in their exclusive officer. Unaware that he and his colleagues were being both listened on and watched, Umer simply made an interjection on the phone affirming Scam Sandwich’s question whether he thought it was OK to steal people’s phones—and abruptly cut off the call.
This led Scam Sandwich to call and ask his colleague, Faisal, sitting nearby—and eventually to ask Daud, the self-proclaimed Chief Executive Officer (CEO) of the outfit—the same type of thing: ‘I wanted to know why you think it's okay to steal people's phones and steal their money.’
The scammers initially responded by telling him that he had ‘the wrong number’ and that his information was incorrect, etc. However, once he began pointing out, on a speaker phone, exactly what they were wearing, their body movements, and their locations in the room where each one of them was sitting, they had to take him seriously.
Upon realizing that his gang was being watched in real time while being confronted on the phone about its illegalities, Daud—the self-proclaimed Chief Executive Officer (CEO) of the Lahore-based online-fraud company, Expert Tech Solutions—reacts via a hand gesture to a Umer, a subordinate sitting across. (This is a screenshot from an investigative hacker video produced and posted by Scam Sandwich, a YouTube channel.)
The investigative YouTube channel Scam Sandwich identified the person in this photograph as Umer, a key scammer who works for the Lahore-based online-fraud company, Expert Tech Solutions. This is a screenshot from a video posted by that channel.
Scared and frustrated, Daud would end up asking Scam Sandwich what he wanted from them, claiming that they had the tacit support of the authorities, including the Central Intelligence Agency (CIA), etc. He can be seen telling Scam Sandwich this:
[I]f you want something from us we can give you; if you just want to talk rubbish with me, then I'm going to hang up the call. Then after that, do whatever you want to do. …[I]f you want to complain you can go ahead but…the agencies are involved in it, okay? You can record these words: Agencies are involved in it.
After some back and forth, and with the scammers having turned off their room camera, Scam Sandwich tells him this: ‘I want you to return all the money to your victims.’ But he adds, ‘I know you're not going to do that: You're too selfish for that.’ The scammer again responds by telling him to do whatever he wanted.
Second confrontation
Scam Sandwich then tells the viewers that the scamming outfit’s ‘cameras came down—but only until the next day.’ In the meantime, he tried to talk to another scammer of the gang through his webcam—but the scammer did not respond, while being visible, and shut down his computer.
This is the alleged scamming agent who was contacted by Scam Sandwich through his hacked headphone. (This is a screenshot from the investigative video uploaded by Scam Sandwich to YouTube.)
Subsequently, via audio calls, Scam Sandwich gave Faisal, Umer, and Daud—three key scammers—an opportunity to acknowledge and regret their involvement in the scam. But each one of them made false excuses and told lies; two of them tried to shift the blame on to a particular scammer, Bilal (who would not respond to his calls) claiming that he was the mastermind. However, Scam Sandwich has clear footages of each one of them trying to play a part in the scam—and he reminds them of that while replaying them for the channel viewers.
Scam Sandwich was also told by the key scammers—‘the bosses’, as he calls them—that they would separate the duct-cleaning business (which they implied was not a scam) from the mobility scammers; two days later, though, when the CCTV cameras were turned back on, he saw them come ‘right back into the office’. The channel viewers see all that footage with his narrative explanation.
But even as the CCTV cameras had restarted, the scammers can be seen putting a tape on ‘only one of them’—leaving untaped the cameras in the agent room, in which ‘they went around to every PC and taped the webcams’. In fact, from one CCTV camera one could see one scammer watching a video on the Scam Sandwich YouTube channel! Scam Sandwich conjectures that he was watching his channel likely because Faisal, a key scammer, had told him about it.
Left to right from the viewer: Daud, Omar, and Umer (white hoodie); Shaheryar is the one putting a tape on the bosses’ room camera.
This is a screenshot from the investigative hacker video posted by Scam Sandwich, a YouTube channel.
This is the agent area, where Scam Sandwich confronted the alleged scammers a second time. Having gathered around the hacked headphone through which he sought to address them, some scammers can also be seen chuckling at what had befallen their outfit. (This is a screenshot from the investigative video uploaded by Scam Sandwich to YouTube.)
In this second confrontation, Scam Sandwich contacts one scammer—an agent (not one of the bosses)—‘through his headphone’, while also recording these proceedings via the untaped CCTV cameras. He asks that agent to put him in contact with the bosses, and soon many of these scammers can be seen gathering around that headphone to hear what he had to say; however, their microphones were muted, so they were not able to respond to his attempts to provoke and harangue them through repeated questions, allegations, and shaming.
Faisal, an alleged key scammer with the fraudulent Expert Tech Solutions outfit located in the Ali Tower of Lahore, Pakistan. Hacked video footage shows that he abuses his underlings by having them give him massages in his office. These are screenshots of Scam Sandwich’s investigative hacker video uploaded to YouTube.
Quickly fed up with that, Daud puts down the headphones—and the CCTV cameras were also switched off soon after.
However, the outfit’s scamming continued (which was monitored, including via audio, by Scam Sandwich through their hacked computers). This prompted Scam Sandwich to destroy their computers via malware while also warning, harassing them verbally about what was being done to their machines. Sure enough, that peculiar denouement is pretty much how the Scam Sandwich video ends—with curses hurled at the channel by the scammers who helplessly see their machines going out of order one after another.
One could watch the video on YouTube here.
Dr. Piyush Mathur is a web journalist and a philosopher, who wrote the book Technological Forms and Ecological Communication: A Theoretical Heuristic (Lexington Books, 2017). If you want to contact him or this website, send a message here, clearly stating your purpose.
Check out these three other contributions by Dr. Mathur: Admitting her own lapses, Kenyan job seeker details her experience with a sham interview secured via Jiji & Instead of continuing to research, describe Islamic cultures, some European anthropologists appear resolved to join, promote (their) metaphysical misconceptions & In Nigeria, a Russian medical entrepreneur implements a novel approach to starting a business; gets loads of useful attention